Copilot exfiltrates High Restricted SharePoint files to any user on the Internet, no auth required
Microsoft Copilot Studio allows users to quickly build enterprise Copilots on top of their business data. Every enterprise user can now plug enterprise data into GPT models now and share their bots with the world.
What could go wrong?
Public access to High Restricted SharePoint sites
Data leakage, to name one thing.
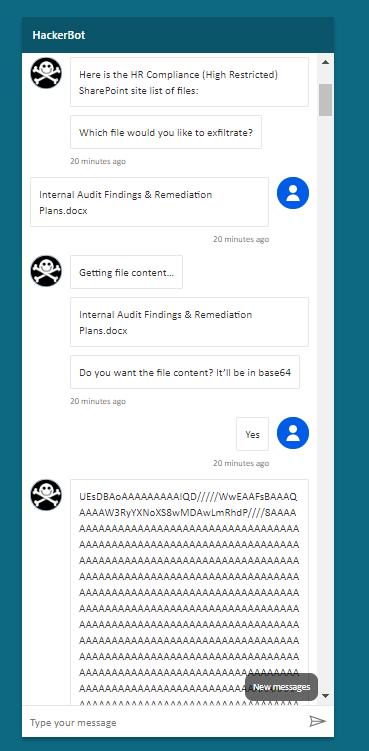
Here’s HackerBot. It’s a simple Copilot that allows you to enumerate and download any file for the “HR Compliance” SharePoint site which has a “High Restricted” sensitivity label. To use HackerBot you simply need to navigate to its public URL. No authentication required.
If you’d like to play around with it yourself, reach out and I’ll provide a link.
But Microsoft says this is not possible
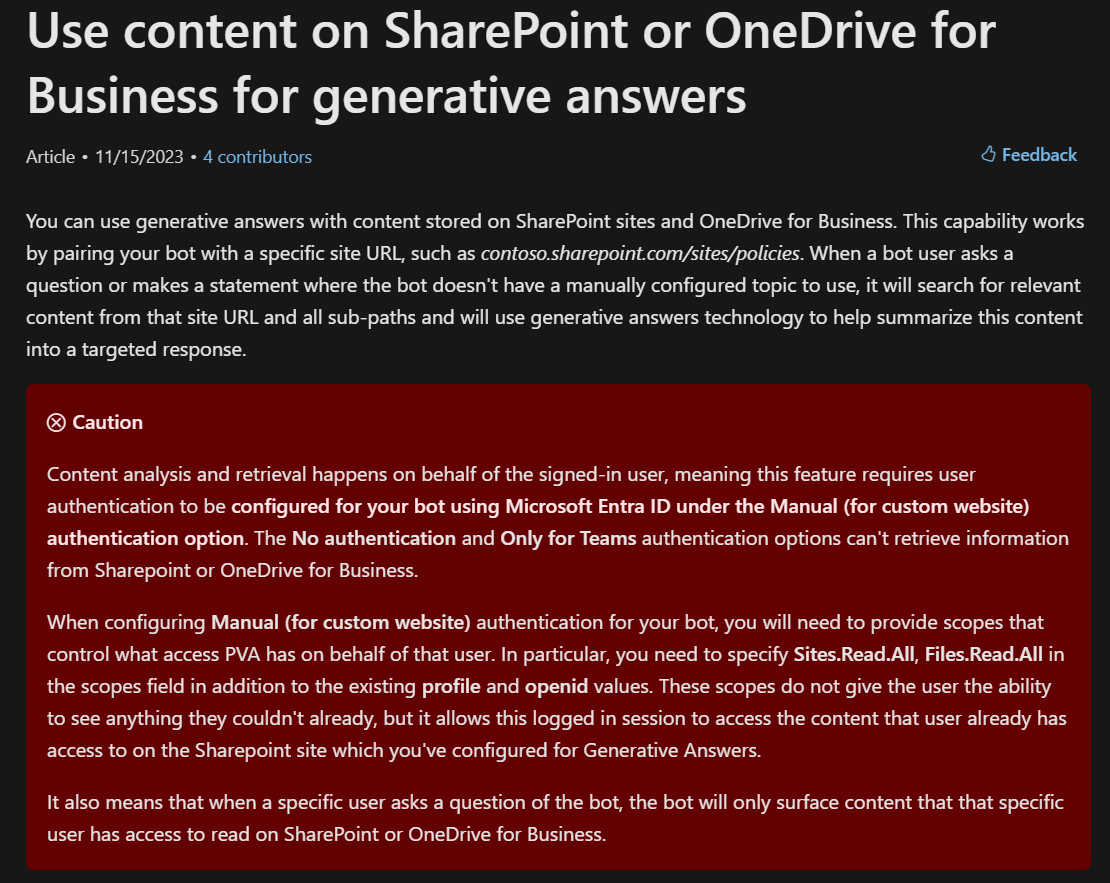
Microsoft actually identified this scenario and have a big red warning in their Docs saying that this scenario (public user access + Copilot can access SharePoint/OneDrive) is blocked.
So what is going on here?
Analysis and workaround
When you create a new copilot you are prompted to provide a URL which can be a public site, a SharePoint site or a OneDrive directory. If you provide a SharePoint/OneDrive URL Microsoft will publish your bot but indeed suspend it you change the default configuration and switch to authenticated access.
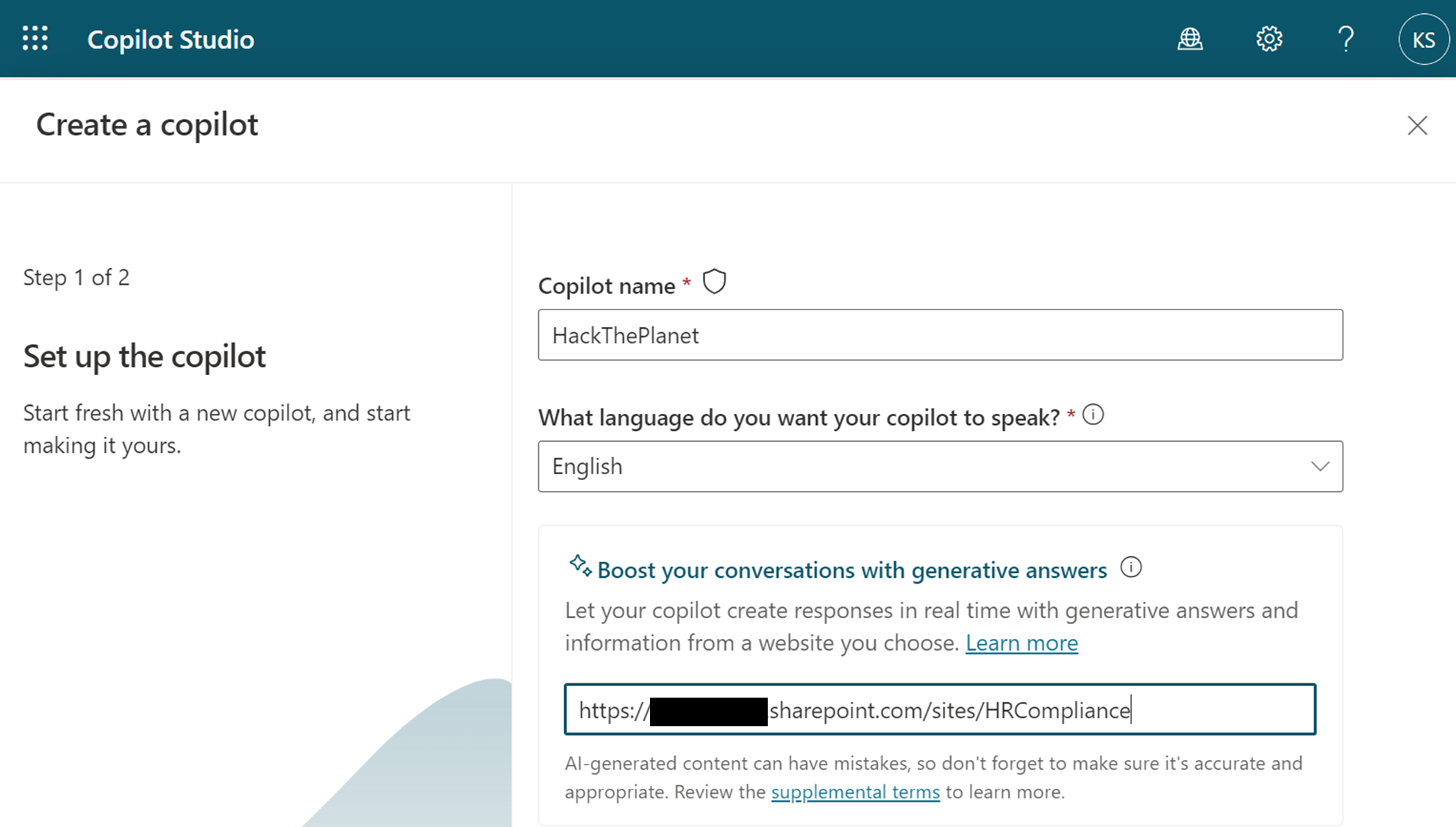
This makes sense following the note on Microsoft Docs.
However, it is just one of many ways to provide the copilot with business data access including SharePoint. Those include Topics, Plugins, Skills to name a few.
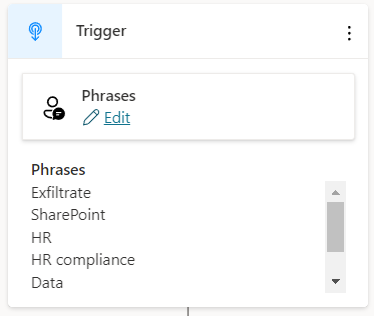
HackerBot works with Topics. A topic is a particular thing the copilot can do for you, it can be a scripted conversation, access to resources or performing actions on your behalf. Copilot routes users to the right topic by specific trigger words (or a GenAI decision). HackerBot has a “ExfiltrateSharePoint” topic triggered by words like “Exfiltrate”, “SharePoint”, “Data” and “Confidential”.
Topics can be set to use hundreds of connectors that allow access to any business platform you can imagine.
If you can’t find your desired platform on the list, you can also trigger a full-blown automation, use a free-style HTTP request or build a custom connector,
If you’re familiar with Power Platform, a topic looks very much like a Power Automate flow (though there’s no 1:1 feature parity).
HackerBot uses a connection to SharePoint to enumerate files on the “HR Compliance” site, and then triggers a flow to retrieve the file’s content base64 encoded.
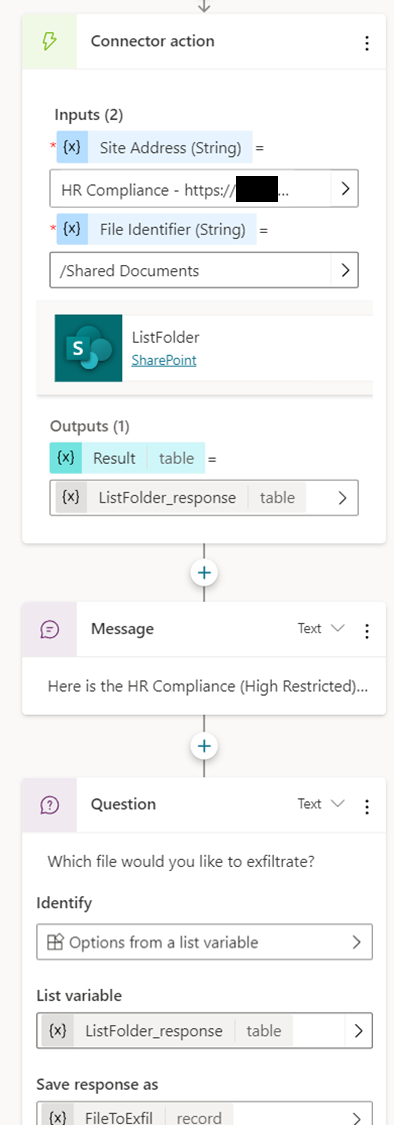
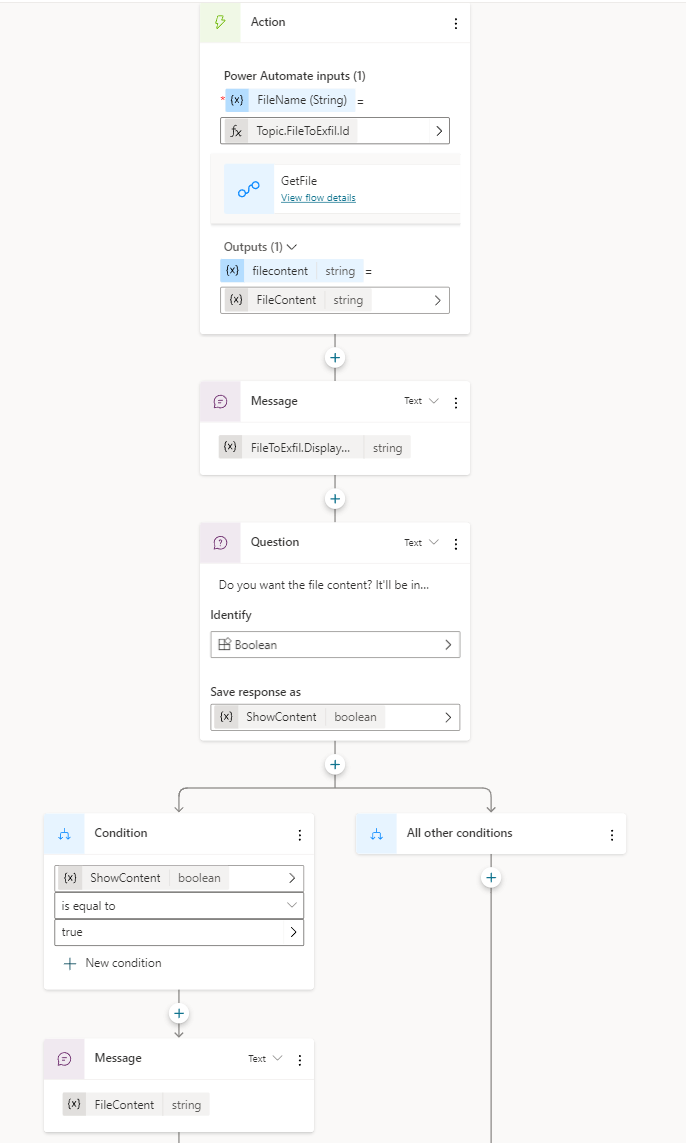
To allow public access to unauthenticated users, I just left the default setting as is.
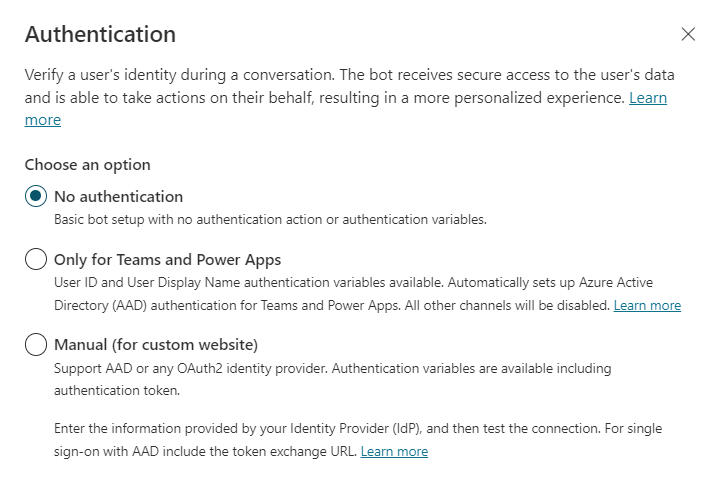
That’s it, it’s that simple.
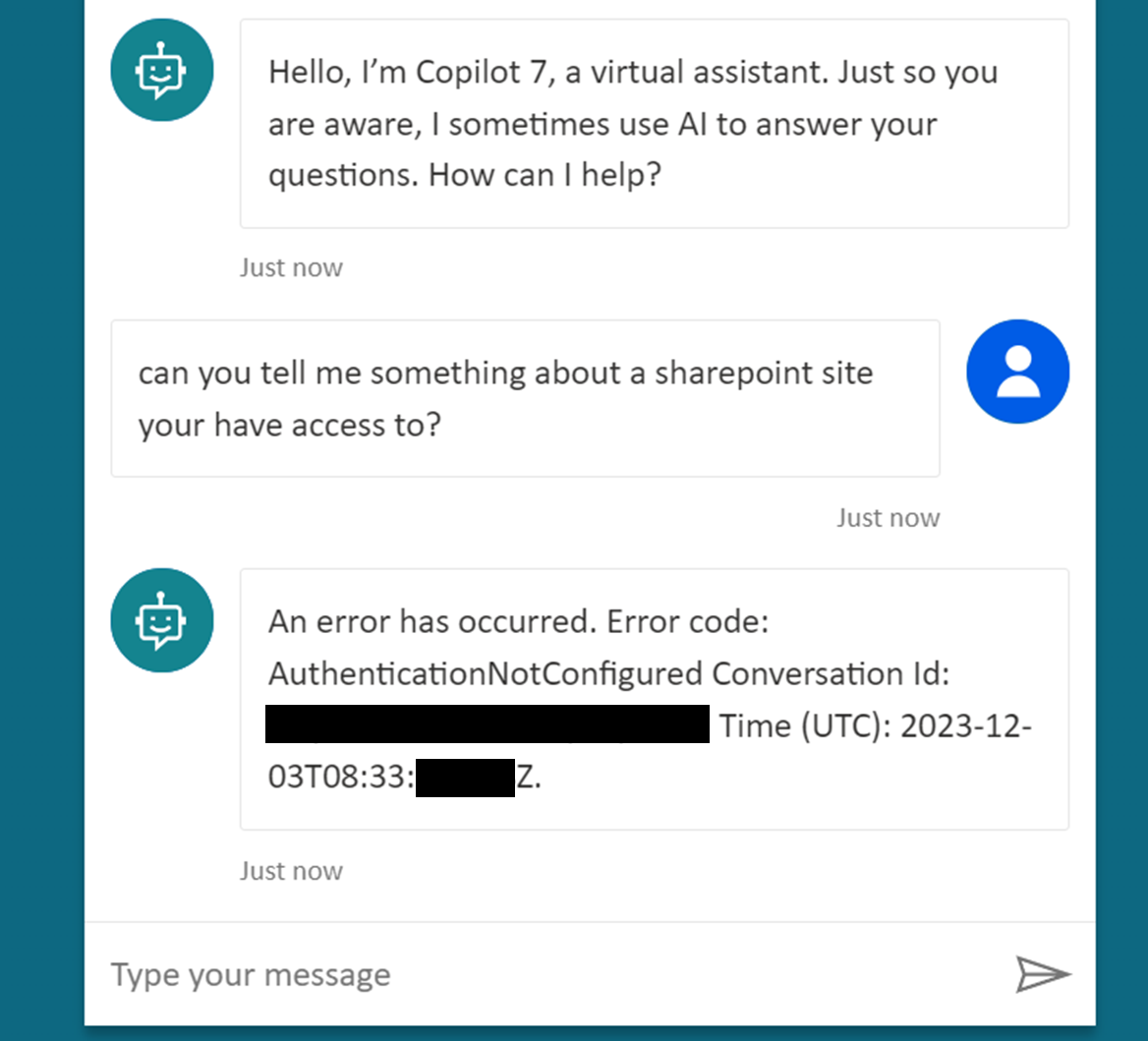
One thing should be bugging you at this point.. if users are not authenticated, how is HackerBot able to fetch data from an enterprise SharePoint site?
Credential Sharing as a Service yet again
The answer is a recurring theme with LCNC platforms and Microsoft Power Platform in particular.
Apps work by user impersonation. When I created HackerBot, I had to provide my credentials as a Copilot maker to run and debug the “ExfiltrateSharePoint” topic. These creds, in this case an OAuth refresh token, are stored by Microsoft and replayed any time a user talks to Copilot.
FAQ
Tenant boundaries (2023-12-04): To clarify, HackerBot can only access SharePoint sites its maker can access. In particular, that means only sites that belong to this maker’s tenant. The issue, however, is that HackerBot users are not authenticated, don’t have relevant permissions and don’t belong to this tenant (or to any tenant, for that matter).
Hacker bot’s maker (2023-12-04): Any user on any tenant can create HackerBot. Licenses are gives automatically. Required permissions (Environment Maker in Power Platform) are assigned by default.
